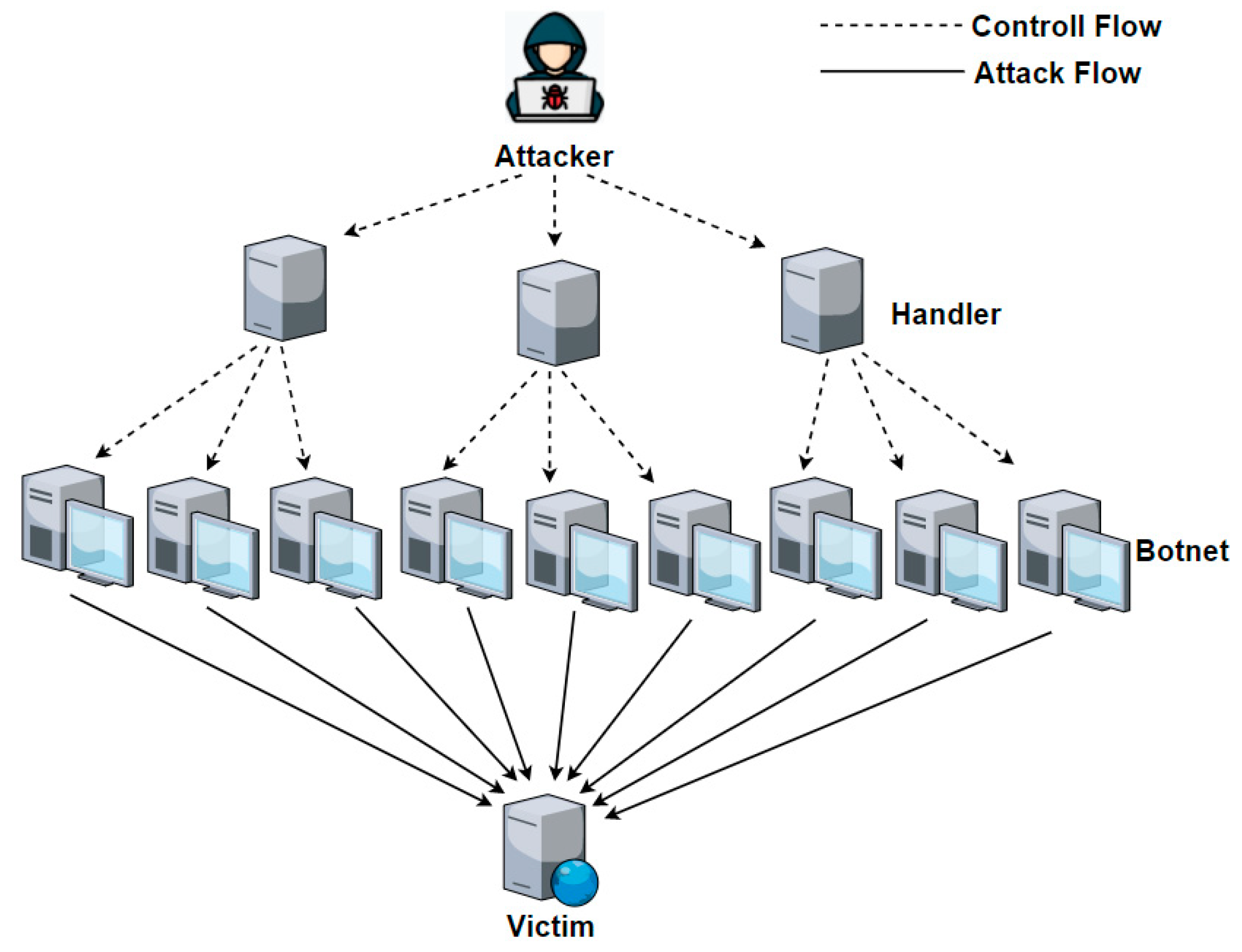
Applied Sciences | Free Full-Text | Detection of Unknown DDoS Attacks with Deep Learning and Gaussian Mixture Model
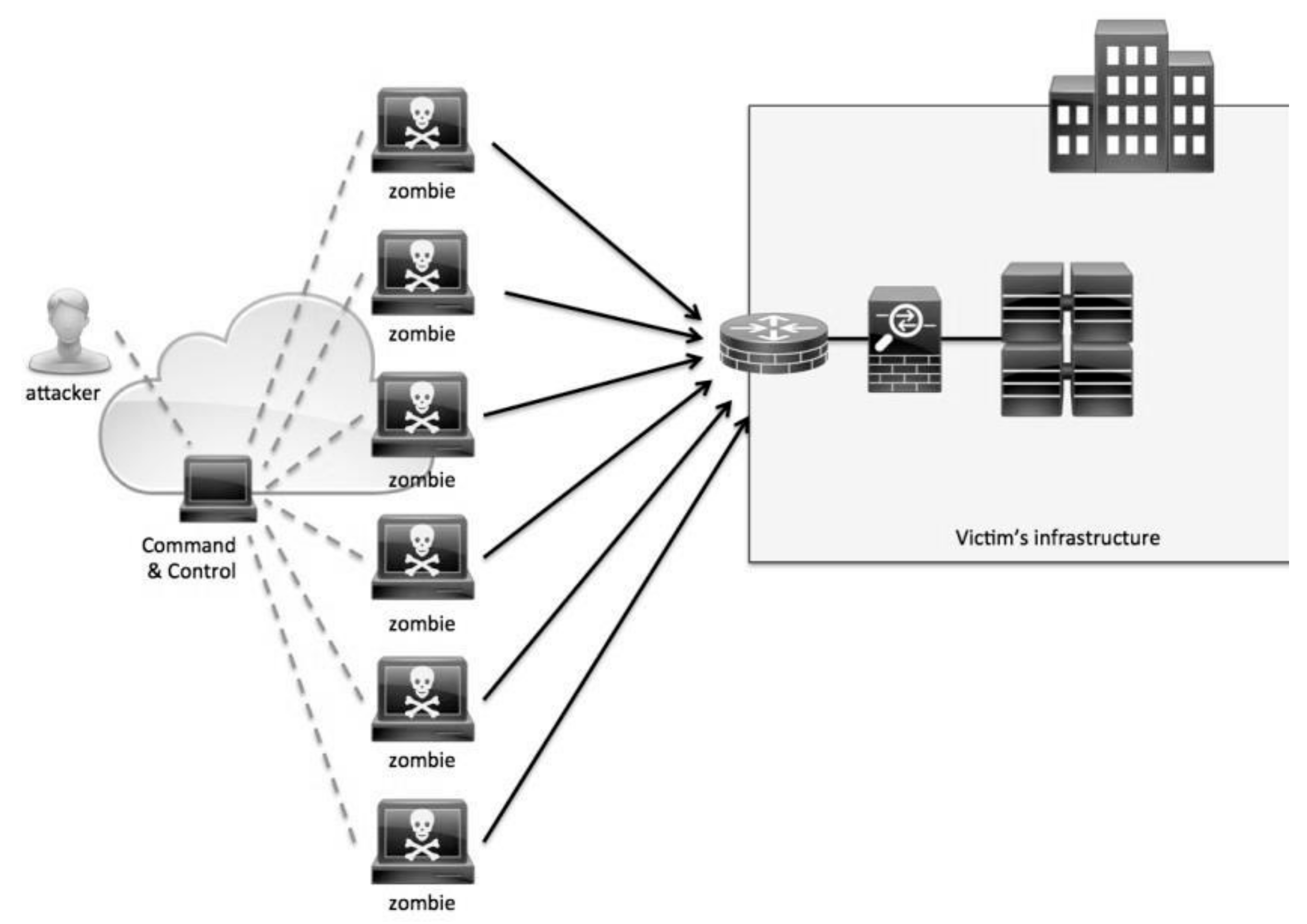
Symmetry | Free Full-Text | Distributed Denial of Service (DDoS) Mitigation Using Blockchain—A Comprehensive Insight

Drones | Free Full-Text | Searching for Scalable Networks in Unmanned Aerial Vehicle Infrastructure Using Spatio-Attack Course-of-Action

Drone demo shows it's possible to protect 5G-managed devices from DDoS, exfiltration attacks | Network World

Shadowserver on X: "Two new daily honeypot drone based DDoS reports have been enabled! Honeypot DDoS Events Report contains info on C2s issuing attack commands to Mirai-like infected IoT devices: https://t.co/iauDYJXrLM Honeypot
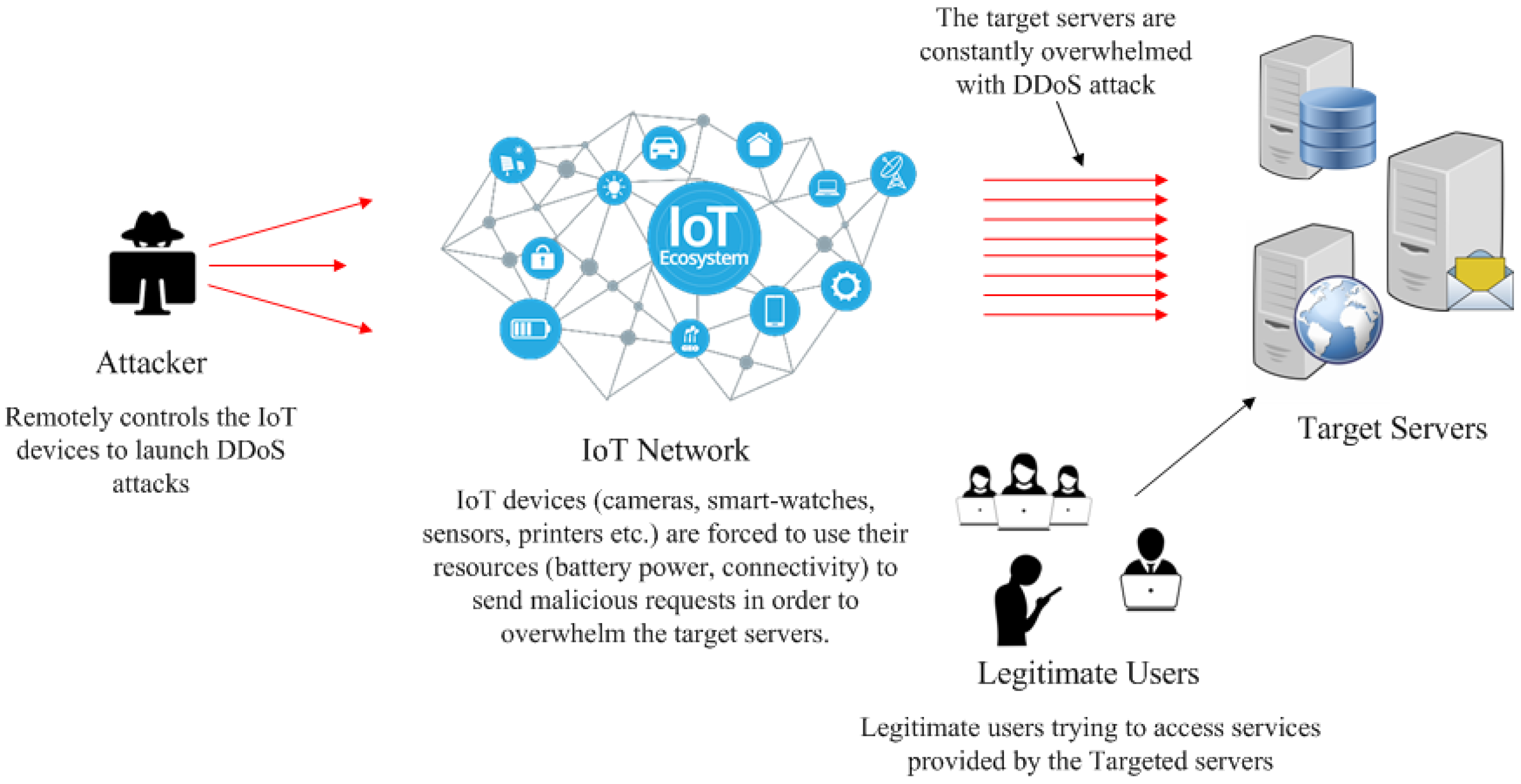
Sensors | Free Full-Text | Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey

Shadowserver on X: "Two new daily honeypot drone based DDoS reports have been enabled! Honeypot DDoS Events Report contains info on C2s issuing attack commands to Mirai-like infected IoT devices: https://t.co/iauDYJXrLM Honeypot
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm
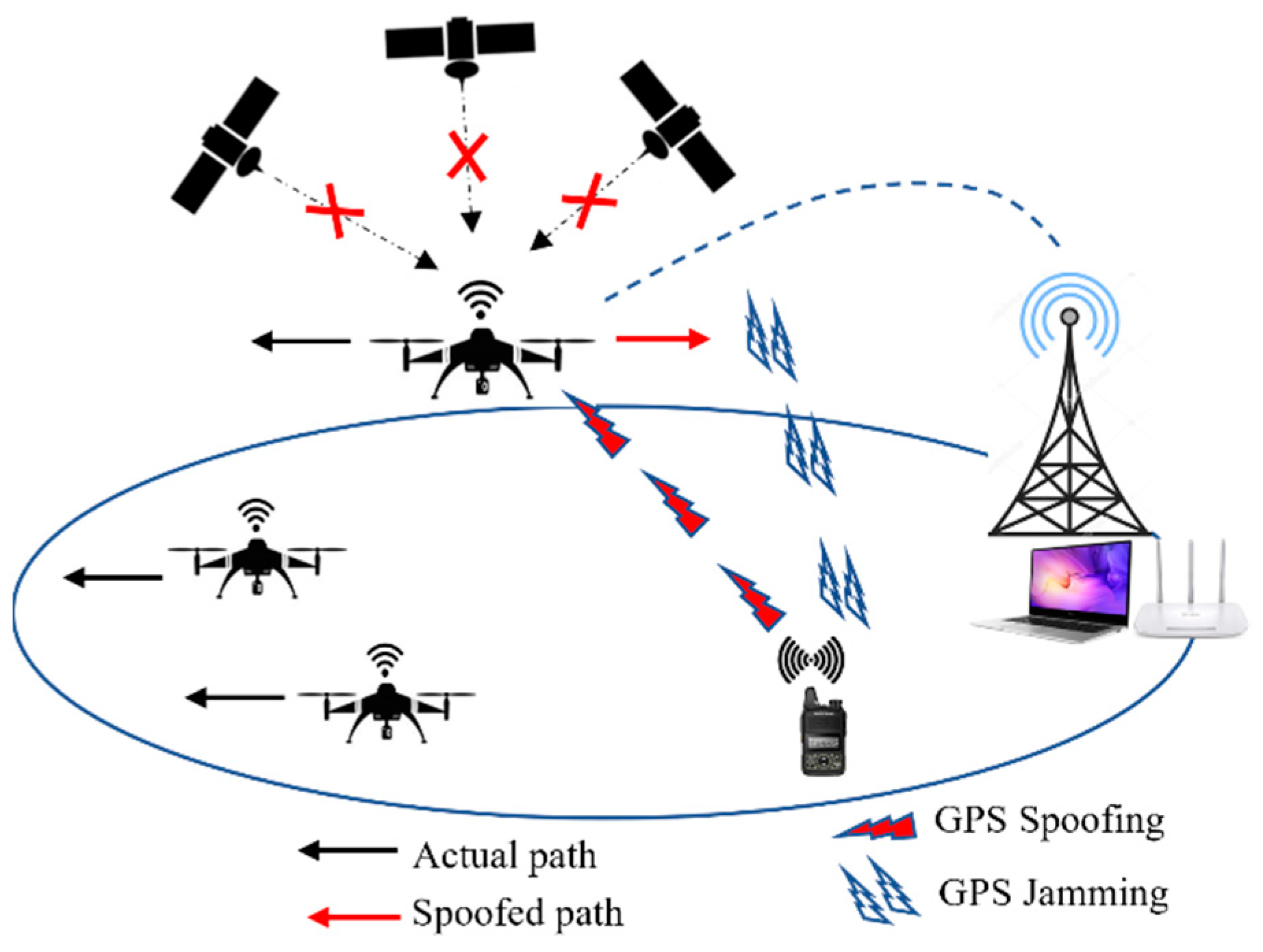
JSAN | Free Full-Text | DDoS Attack and Detection Methods in Internet-Enabled Networks: Concept, Research Perspectives, and Challenges





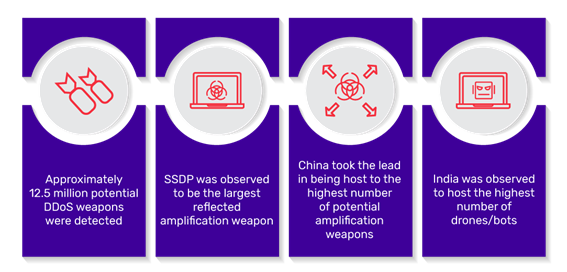
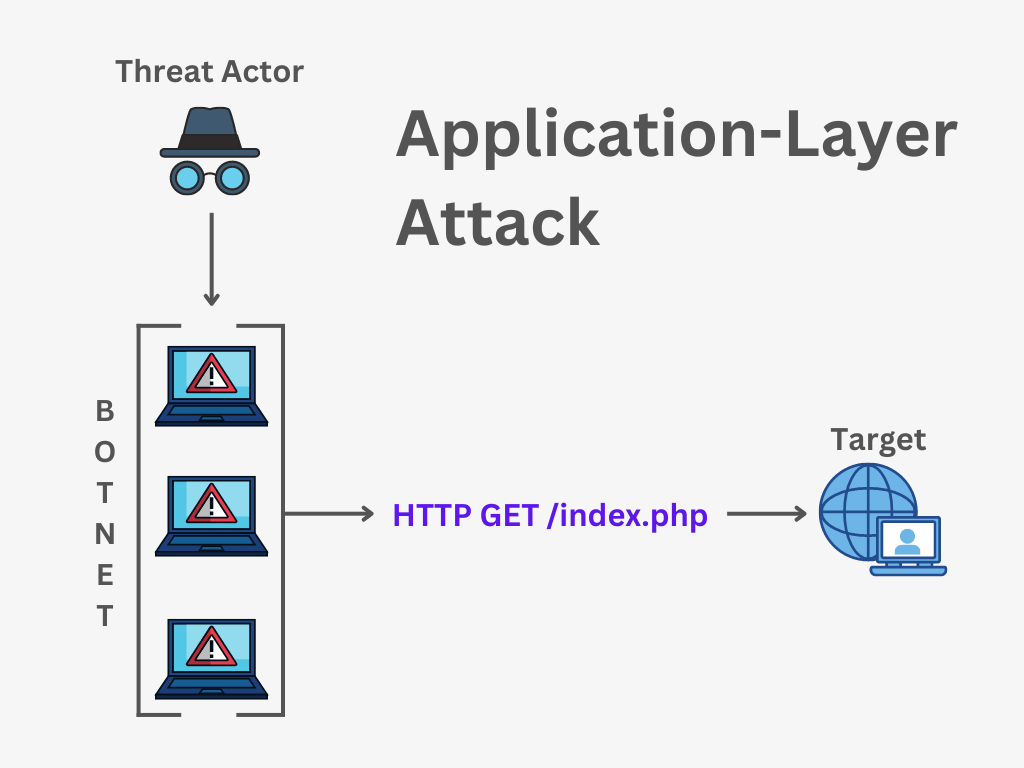

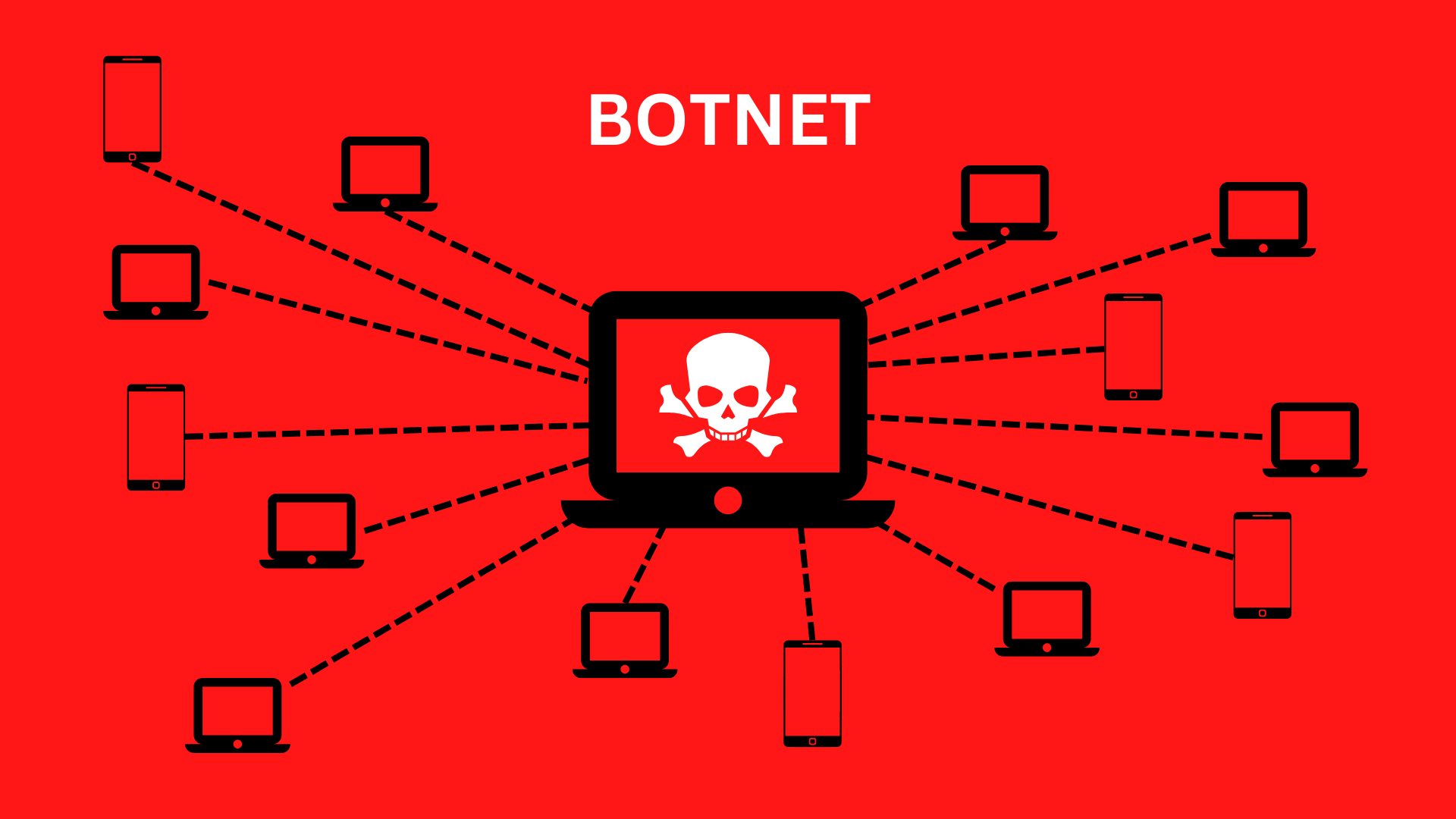

![Denial of service (DoS) attack [78] | Download Scientific Diagram Denial of service (DoS) attack [78] | Download Scientific Diagram](https://www.researchgate.net/publication/349419829/figure/fig2/AS:1001946601238529@1615894093911/Denial-of-service-DoS-attack-78.png)



![PDF] The Impact of DoS Attacks on the AR.Drone 2.0 | Semantic Scholar PDF] The Impact of DoS Attacks on the AR.Drone 2.0 | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/3eaba6abfaf1bb8c712b7a2bd8baaad5d8dec2ef/3-Figure1-1.png)